I’ve done some thinking about computer security and privacy over the past while. It’s been precipitated by conversations with Gust Mees. It’s good thinking.
We’re all in the same boat. Just think of the number of times you’ve clicked the checkbox beside this.
- My team of lawyers and I have read and studied your terms and conditions and we’re cool with agreeing to your rules and the fact that you’ll be accessing some of my private information on this device.
I know that you’ve done it because you’re using a computer with an operating system and a web browser so you’ve already done the above twice. (Unless, of course, you’re using someone else’s computer and they’ve already given permission on your behalf.)
This morning’s reading led me to a free application called “Permissions Explorer“. Of course, my lawyers and I looked through the individual applications as they were being installed but once installed, they’ve got a little out of mind.
I installed it this morning and liked its legal terms –
“/* No permission required to use this app, no ads. Does only what you want it to do */”
So, I decided to put it through its paces. I was quite impressed with its completeness.
Upon first launch, a menu indicates just what areas of privacy/security it will investigate.
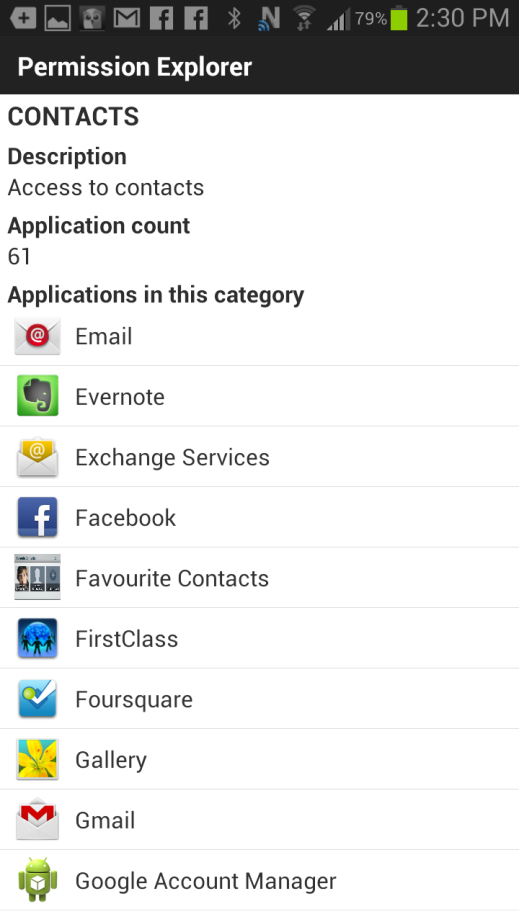
Ever curious, I decided to work my way through them. For example, what 61 applications do I have that have access to my contacts?
As I looked through them, I can see why. After all, FirstClass and Gmail are the two email systems that I use on a daily basis. It only makes sense that they have access to my contacts. It was through exploring the rest of the applications that I became intrigued and really immersed in the exercise.
The next step is to ascertain what resources the applications have permission to use.
Interesting! I’ve got 66 ways to vibrate this device.
Look at the number that have access to the internet. They will all have their purpose – Internet browsers, of course. Email clients, for sure. FourSquare? That’s how you’ll know that I’m walking the dog at the Navy Yard. It’s interesting to go through the list and wonder about some of the less obvious ones.
There were a few surprises in the exercise but, for the most part, the results made a great deal of sense. I’d really like to lay my hands on similar applications for all the major devices.
In the classroom, I think that they could be used very successfully to generate an awareness and a discussion about how students are connected and just what that means.
It would even be an enlightening exercise to generate a report and then look at all the applications that are on school or home provided computers and classify them as “necessary”, “unnecessary”, or “I wonder why”.
It might even generate more interest in looking at the legal terms and conditions the next time you install an application or sign up for a web service.
Related articles
- [News] Answer Line: Creepy permissions for Android apps (pcworld.in)
- Twitter Fixes Bug That Allowed Third-Party Apps to Access DMs Without Permission (news.softpedia.com)
- Third-party apps bypass Twitter security to access private data (itproportal.com)
- Yahoo! Hack Demonstrates the Risks Posed by Third-Party Code in Cloud Computing (news.softpedia.com)
- Answer Line: Creepy permissions for Android apps (pcworld.com)
- 10 Efficient And Minimal Android Apps That You May Not Have Heard About (makeuseof.com)
- Mobile Apps are getting sneaky (thehindu.com)
- Path Fined by the FTC over Kid Privacy Issues, Just as a New Privacy Flaw Emerges (news.softpedia.com)
- Google is sued by dozens of customers after ‘snooping on 10million iPads and mobiles’ (dailymail.co.uk)
- You cannot trust social media to keep your private data safe: Story of a Twitter vulnerability (ioactive.com)



Please share your thoughts here. I’d enjoy reading them.